UGC NET CS 2013 Dec-paper-2
Question 1 |
When data and acknowledgement are sent in the same frame, this is called as
Piggy packing | |
Piggy backing | |
Backpacking | |
Good packing |
Question 1 Explanation:
→ In two-way communication, wherever a frame is received, the receiver waits and does not send the control frame (acknowledgement or ACK) back to the sender immediately.
→ The receiver waits until its network layer passes in the next data packet. The delayed acknowledgement is then attached to this outgoing data frame.
→ This technique of temporarily delaying the acknowledgement so that it can be hooked with next outgoing data frame is known as piggybacking.
→ The receiver waits until its network layer passes in the next data packet. The delayed acknowledgement is then attached to this outgoing data frame.
→ This technique of temporarily delaying the acknowledgement so that it can be hooked with next outgoing data frame is known as piggybacking.
Question 2 |
Encryption and Decryption is the responsibility of _______ Layer.
Physical | |
Network | |
Application | |
Datalink |
Question 2 Explanation:
Presentation layer is responsible for
1. Translation, authentication
2. Encryption and Decryption
3. Compression and decompression
But according application layer also can do these responsibilities. So, Optio-C is the correct answer.
1. Translation, authentication
2. Encryption and Decryption
3. Compression and decompression
But according application layer also can do these responsibilities. So, Optio-C is the correct answer.
Question 3 |
An analog signal carries 4 bits in each signal unit. If 1000 signal units are sent per second, then baud rate and bit rate of the signal are and
4000 bauds \ sec & 1000 bps | |
2000 bauds \ sec & 1000 bps | |
1000 bauds \ sec & 500 bps | |
1000 bauds \ sec & 4000 bps |
Question 3 Explanation:
→ Bit rate is nothing but number of bits transmitted per second
→ Baud rate is nothing but number of signals units transmitted per unit time.
Given data,
-- Bit rate of a signal=4000 bps
-- Each signal unit carries=4 bits
-- Baud rate=?
Step-1: Baud rate= Bit rate of signal / baud rate
= 4000/4 bps
= 1000 bps
Step-2: Bit rate= Number of bits transmitted per second*number of signals units transmitted per unit time
= 4*1000 bps
= 4000 bps
→ Baud rate is nothing but number of signals units transmitted per unit time.
Given data,
-- Bit rate of a signal=4000 bps
-- Each signal unit carries=4 bits
-- Baud rate=?
Step-1: Baud rate= Bit rate of signal / baud rate
= 4000/4 bps
= 1000 bps
Step-2: Bit rate= Number of bits transmitted per second*number of signals units transmitted per unit time
= 4*1000 bps
= 4000 bps
Question 4 |
The VLF and LF bauds use _______ propagation for communication.
Ground | |
Sky | |
Line of sight | |
Space |
Question 4 Explanation:
The VLF and LF bauds use ground propagation for communication.
Propagation methods are 3 types
1. Ground
2. Sky
3. Line of sight
→ Very low frequency or VLF is for radio frequencies (RF) in the range of 3 to 30 kilohertz (kHz), corresponding to wavelengths from 100 to 10 kilometers, respectively.
→ The low-frequency signals travel in all directions from the transmitting antenna.
Propagation methods are 3 types
1. Ground
2. Sky
3. Line of sight

→ Very low frequency or VLF is for radio frequencies (RF) in the range of 3 to 30 kilohertz (kHz), corresponding to wavelengths from 100 to 10 kilometers, respectively.
→ The low-frequency signals travel in all directions from the transmitting antenna.
Question 5 |
Using the RSA public key cryptosystem, if p = 13, q = 31 and d = 7, then the value of ‘e’ is
101 | |
103 | |
105 | |
107 |
Question 5 Explanation:
Step-1: Compute n=p*q
= 13*31
= 403
Step-2: Compute f(n)= (p − 1)(q − 1)
= 12*30
= 360
Step-3: Compute d = e-1 mod f(n)
Choose an e such that 1
d.e = 1 mod f(n)
e = 1 mod 360
= 361 mod 360
= 721 mod 360
Note: Given d=7
7*e= 721 mod 360
e=103
= 13*31
= 403
Step-2: Compute f(n)= (p − 1)(q − 1)
= 12*30
= 360
Step-3: Compute d = e-1 mod f(n)
Choose an e such that 1
e = 1 mod 360
= 361 mod 360
= 721 mod 360
Note: Given d=7
7*e= 721 mod 360
e=103
Question 6 |
FAN IN of a component A is defined as
Number of components that can call or pass control to component A. | |
Number of components that are called by component A. | |
Number of components related to component A. | |
Number of components dependent on component A. |
Question 6 Explanation:
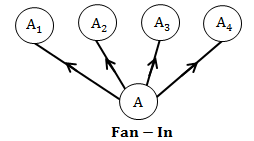
→ FAN IN of a component A is defined as number of components that can call or pass control to component A.
→ FAN-IN defines “number of modules directly invoking given module”.
→ FAN OUT is the number of classes used by a certain class or the number of methods called by a certain method.
→ FAN OUT defines “Number of modules that are directly controlled by given module.
→ Good software design require High FAN-IN and LOW FAN-OUT
→ FAN-IN defines “number of modules directly invoking given module”.

→ FAN OUT is the number of classes used by a certain class or the number of methods called by a certain method.
→ FAN OUT defines “Number of modules that are directly controlled by given module.
→ Good software design require High FAN-IN and LOW FAN-OUT

Question 7 |
The relationship of data elements in a module is called
Coupling | |
Modularity | |
Cohesion | |
Granularity |
Question 7 Explanation:
→ Cohesion is a measure of internal strength within a module and relationship of data elements in a module, whereas coupling is a measure of inter dependency among the modules.
→ In the context of modular software design there should be high cohesion and low coupling.
→ In the context of modular software design there should be high cohesion and low coupling.
Question 8 |
Software Configuration Management is the discipline for systematically controlling
the changes due to the evolution of work products as the project proceeds. | |
the changes due to defects (bugs) being found and then fixed. | |
the changes due to requirement changes | |
all of the above |
Question 8 Explanation:
Software Configuration Management is the discipline for systematically controlling
1. The changes due to the evolution of work products as the project proceeds.
2. The changes due to defects(bugs) being found and then fixed.
3. The changes due to requirement changes
1. The changes due to the evolution of work products as the project proceeds.
2. The changes due to defects(bugs) being found and then fixed.
3. The changes due to requirement changes
Question 9 |
Which one of the following is not a step of requirement engineering ?
Requirement elicitation | |
Requirement analysis | |
Requirement design | |
Requirement documentation |
Question 9 Explanation:
Requirements engineering (RE) refers to the process of defining, documenting and maintaining requirements in the engineering design process.
Requirement Analysis Steps:
1. Requirements inception or requirements elicitation: Developers and stakeholders meet, the latter are inquired concerning their needs and wants regarding the software product.
2. Requirements analysis and negotiation: Requirements are identified (including new ones if the development is iterative) and conflicts with stakeholders are solved. Both written and graphical tools (the latter commonly used in the design phase but some find them helpful at this stage, too) are successfully used as aids.
3. System modeling: Some engineering fields (or specific situations) require the product to be completely designed and modeled before its construction or fabrication starts and, therefore, the design phase must be performed in advance.
4. Requirements specification: Requirements are documented in a formal artifact called a Requirements Specification (RS), which will become official only after validation.
5. Requirements validation: Checking that the documented requirements and models are consistent and meet the needs of the stakeholder. Only if the final draft passes the validation process, the RS becomes official.
6. Requirements management: Managing all the activities related to the requirements since inception, supervising as the system is developed and, even until after it is put into use (e. g., changes, extensions, etc.)
Requirement Analysis Steps:
1. Requirements inception or requirements elicitation: Developers and stakeholders meet, the latter are inquired concerning their needs and wants regarding the software product.
2. Requirements analysis and negotiation: Requirements are identified (including new ones if the development is iterative) and conflicts with stakeholders are solved. Both written and graphical tools (the latter commonly used in the design phase but some find them helpful at this stage, too) are successfully used as aids.
3. System modeling: Some engineering fields (or specific situations) require the product to be completely designed and modeled before its construction or fabrication starts and, therefore, the design phase must be performed in advance.
4. Requirements specification: Requirements are documented in a formal artifact called a Requirements Specification (RS), which will become official only after validation.
5. Requirements validation: Checking that the documented requirements and models are consistent and meet the needs of the stakeholder. Only if the final draft passes the validation process, the RS becomes official.
6. Requirements management: Managing all the activities related to the requirements since inception, supervising as the system is developed and, even until after it is put into use (e. g., changes, extensions, etc.)
Question 10 |
Testing of software with actual data and in actual environment is called
Alpha testing | |
Beta testing | |
Regression testing | |
None of the above |
Question 10 Explanation:
→ Alpha test: is conducted at the developer’s site by end-users and conducted in a controlled environment
→ Beta test: is conducted at end-user sites and it is a “live” application of the software in an environment that cannot be controlled by the developer
→ Regression test: Testing is an important strategy for reducing “side effects” when major change is made to the software
→ Beta test: is conducted at end-user sites and it is a “live” application of the software in an environment that cannot be controlled by the developer
→ Regression test: Testing is an important strategy for reducing “side effects” when major change is made to the software
Question 11 |
The student marks should not be greater than 100. This is
Integrity constraint | |
Referential constraint | |
Over-defined constraint | |
Feasible constraint |
Question 11 Explanation:
Integrity constraint have some rules:
1. Every table have at least one attribute as primary key
2. No prime attribute should ever have null value.
The above example given condition but it is not referring any table. So, it is not referential constraints. Other two are not relevant to this question.
So, Option-A is correct answer.
1. Every table have at least one attribute as primary key
2. No prime attribute should ever have null value.
The above example given condition but it is not referring any table. So, it is not referential constraints. Other two are not relevant to this question.
So, Option-A is correct answer.
Question 12 |
GO BOTTOM and SKIP-3 commands are given one after another in a database file of 30 records. It shifts the control to
28th record | |
27th record | |
3rd record | |
4th record |
Question 12 Explanation:
GO BOTTOM command will directly reach end of the record. Here, total number of records are 30. GO BOTTOM command will reach 30th position.
After SKIP-1, it became 29
After SKIP-2, it became 28
After SKIP-3, it became 27.
In question, they given 3 SKIP operations.
After SKIP-1, it became 29
After SKIP-2, it became 28
After SKIP-3, it became 27.
In question, they given 3 SKIP operations.
There are 12 questions to complete.
